A few weeks ago, we wrote about the coming onslaught of AI powered spear phishing email campaigns, where highly convincing emails could be generated by AI and sent out by rented phishing services.
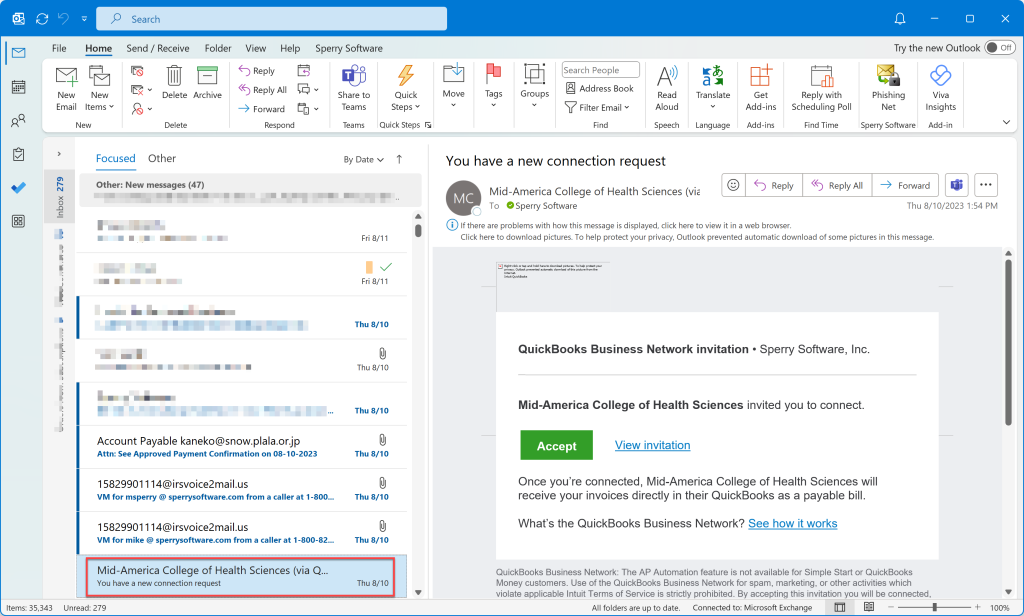
And then last week we noticed in our own main mailbox our first pretty good fake email:
You can see the fake email from “Mid-America College of Health Sciences (via QuickBooks)” (along with 3 (three!) other phishing emails that made it through Microsoft’s Defender for Office 365). Because we frequently receive emails from unknown or first time senders in course of our business, this one was pretty convincing, and I considered the email and the value of accepting the sender’s request as my mouse hovered over the button…
This month, we are introducing our own tool that uses AI to help you to fight phish emails the Phishing Net AI for Microsoft 365.
This tool uses AI to examine emails – in particular at the source of the problem, the URLs contained in the email. This is because the number one thing that hackers need you to do is to click on links contained in the email and embedded in any images.
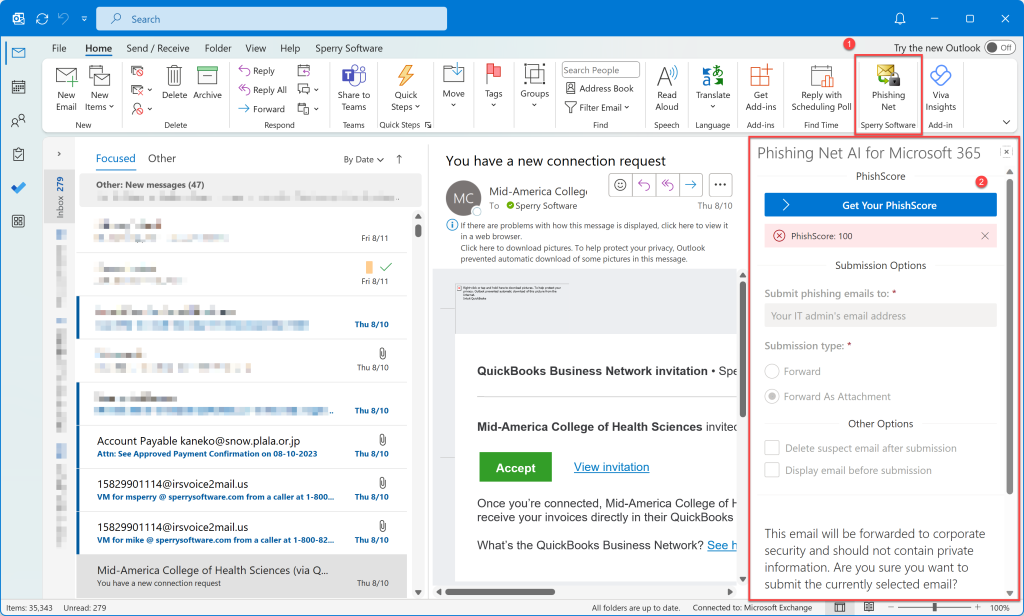
After the AI examines the URL links, the Phishing Net AI add-in displays a PhishScore™, which represents the likelihood that the links contained in the email are malicious. Any PhishScore™ from 1 to 50 is displayed in green meaning it’s ok, a score from 51-75 is displayed as a warning in yellow, and a score of 76 or higher is displayed in red to make it easy to see that the email is a phish attempt.
For example, as my mouse hovered over the hacker’s email and I debated clicking on the accept button, instead I clicked on the Phishing Net AI toolbar button, and I was able to spot the fake email easily:
A previous version of this add-in made it easy to submit suspicious emails, and we’ve kept this simple process the same – it’s still just one click to submit the phishing email. This is important because it’s all too easy to just ignore the email, or to accidently click on a link. Plus, not reporting the suspicious email makes it easier for the next attack because other people in the same organization may not be aware of the email – yet the attacker may have sent the same email to many people in the same company (and as an aside, that’s why the add-in, once it examines an email, begins to collect a list of the known bad URLs and checks that list first – so the more the add-in is used in a particular organization, the better it gets).
Also, the previous version had the settings to submit the phishing email right there in the task pane in Outlook. Now, while the settings are still there, they are shown disabled. This is to help administrators as they deploy the add-in, to standardize on a set of options. So, you might be wondering how can these options be changed? The answer is that we are also rolling out a new dashboard (or portal) to allow you to control all the options and settings for yourself or for your users.
Using the Phishing Net AI dashboard, you can set all the options that were available before including the ability to forward the suspicious email as an attachment on a pre-addressed email template, to delete the suspect email or not after submitting it, and of course the ability to also submit to other governing agencies like the FTC, DHS, or Microsoft’s phishing reporting address.
Best of all, this add-in has a free tier. The caveat? You must sign up for Phishing Net AI through Microsoft’s AppSource, meaning you must have a Microsoft 365 account. You can install the add-in into Outlook by clicking on the link above or by clicking the Get Add-Ins toolbar button in Outlook, then searching for “Sperry”. Be sure to choose the Phishing Net AI add-in, and not our flagship product, Safeguard Send. Then choose your tier (the free one is at the bottom).
We hope that by also including a free tier, that we can all be better equipped to fight the coming onslaught of AI based spear phishing email campaigns.